Windows has always been a preferred goal for hackers, but it seems that they now find out how to actively target the MAC. We have seen a dangerous growth MAC computer affecting malwarePersonal data and cryptocurrency stealing.
The danger actors are now using AI with detailed social engineering tricks to target Apple users, and the company is not doing much about it. Meanwhile, a cyber security report has identified a new Mac malware called Frigidstaler, which spreads through fake browser updates and compromise websites.
Be preserved and notify! Get safety alert and specialist technology tips – Now sign up for Kurt’s The Cybergui report.
Image of a mac laptop (Kurt “Cybergui” Notson)
What you need to know
A new malware stray Macos called Frigidsteler is targeting users as part of a comprehensive campaign including fake update scams, cyber security firm proofpoints InformedThe frigidsteler spreads through compromised websites that display the misleading browser update prompt. When users click on these signs, they inadvertently download a malicious DMG file. Once executed, the malware requests the user’s system password to obtain high privileges before stealing sensitive information, including browser cookies, password -related files, cryptocurrency data and Apple notes.
Proofpoint identified two new threat actors behind the operation: TA2726, which serves as traffic distribution service provider, and TA2727, which provides Mac users Frigidsteler. The campaign also deploys malware on Windows and Android devices, pointing to a multi-platform attack strategy. The cyber security firm evaluated with high confidence that TA2726 also distributes traffic for other malware campaigns. Some operations responsible for the first TA569 are now revived under TA2726 and TA2727.
TA569 – also known as mustard template, gold prelood and purple Vallahund – is connected to Cybercrime Syndicate Evilcorp and was first identified in 2022.
Proofpoint also assessed with moderate belief that TA2727 buys traffic through online forums to spread malware, which may be of their own or potential customers.
The report stated, “These are traffic sellers and malware distributors and have been seen in compromise website campaigns such as many web-based attack chains,” including those using fake updated-themed lur. ,
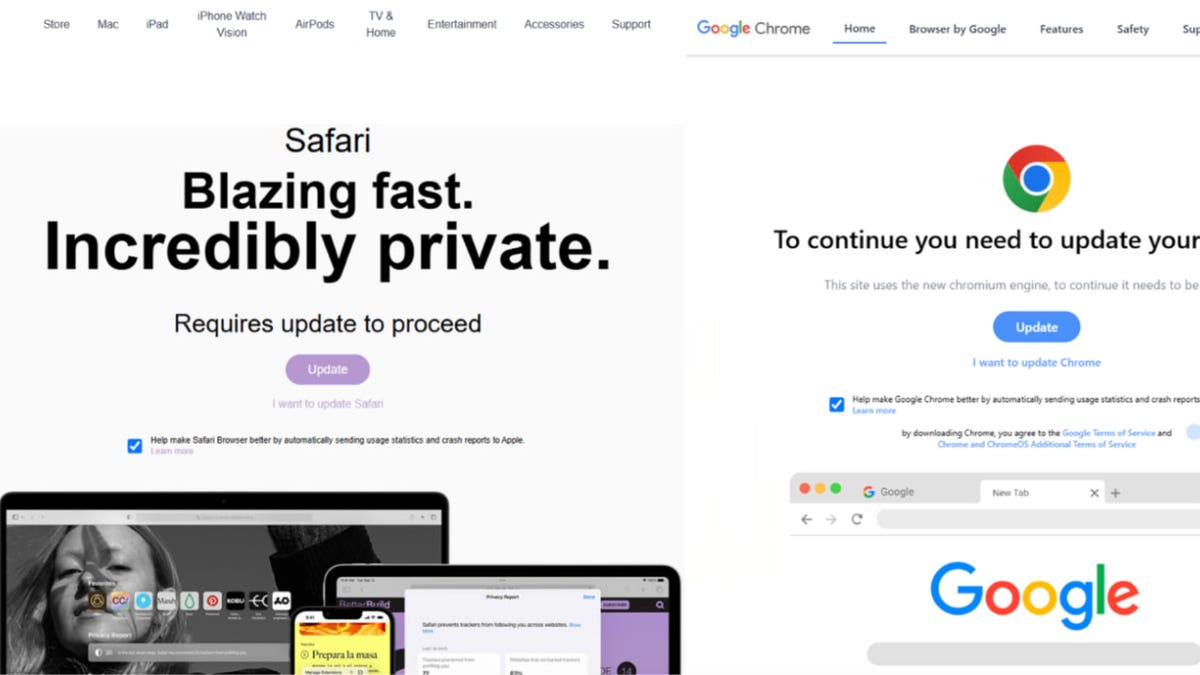
Fake updated greed, distributing frigidstalers through safari, left and chrome, right (proofpoint) (Kurt “Cybergui” Notson)
Best Antivirus for Mac, PC, iPhone, Android – Cybergui Pix
Infostealers are growing
Threatening intelligence stage banana Informed Hackers using Lumma with Lumma, Redline and other infostealers, infect 4.3 million machines in 2024, compromising an estimated 330 million credentials. Security researchers also broadcast 3.9 billion credentials in lists that originate from the Infoselor Log.
Infostealer Malware is expected to be consistently threatened in 2025. On growth with malware-e-Services platforms, infoals, cyber criminals, will probably continue to trust them as a primary tool for credentials and infiltrating systems.

A man is working on his Mac laptop (Kurt “Cybergui” Notson)
From tickets to trouble: how your online data can be made weapons against you
4 ways to stay safe from infostealer malware
Since infostealer malware is growing in sophistication, it is more important to take active steps to protect your data than ever. Here four important methods are given to protect themselves from dangers such as frigidstalers, lumma and other credential-facing malware.
1) Beware of fake software updates: One of the most common infection methods is through misleading browser updated signals. Never download the update from pop-up or random websites. Instead, always update your software directly from official sources, such as the official website of the app store or application. If doubt, check me Detailed guide on how to update your device and software,
2) Enable two-factor authentication (2fa): Even if your credibility is stolen, 2fa The secondary verification method adds an additional layer of protection by the need for the method, such as a one -time code is sent to your phone. Use 2FA for all important accounts including email, banking and cloud services.
3) Use password manager: Many infostealers target passwords saved in web browsers. Instead of relying on your browser to store credentials, use a dedicated Password managerFind out more about me 2025 Best Expert-Recipe Password Managers,
4) Be cautious with downloads and links. Use a strong antivirus: Infostealer Malware often spreads through malicious downloads, fishing emails and fake websites. Avoid downloading software or files from uncontrolled sources and always link a double-checked link before clicking them. The attackers disguised malware as legitimate software, game cheating or torn applications, so it is best to stick to the official websites and app stores for download.
The best way to protect yourself from malicious links that installs malware, potentially reaches your personal information, is a strong antivirus software installed on all your devices. This security can also make you alert for email and ransomware scams, keeping your personal information and digital assets safe. Get my pics for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices,
Has cruceless hackers stole 110 million AT and T customers here
Kurt’s key to Techway
Just as digital scenario develops, similarly we have to face the dangers that come before us. Frigidstealer is just the latest reminder that no platform, not even MACOS, is immune for the growing sophistication of cyber criminal. In 2024, Infosellers, such as Lumma, Stalak and Redline, already compromised with millions of equipment and billions of credibility, the rise of AI-powered attacks and social engineering scams further indicates a challenging road.
Do you think companies like Apple should do more to combat these developed dangers? Write us and tell us Cyberguy.com/Contact.
For my tech tips and security alert, subscribe to my free cybergui report newsletter Cyberguy.com/newsletter,
Ask Kurt a question or tell us which stories you want to cover us,
Follow Kurt on your social channels:
Answers to the most asked cyber questions:
New from Kurt:
Copyright 2025 cyberguy.com. All rights reserved.


