In the ongoing debate about printer safety, some original tool manufacturers (OEMS) have expressed concern about cyber security risks associated with third -party sticking cartridges. However, the reality is that these concerns are often eliminated and presented incorrectly. Let us break why the cartridges not creating an important cyber security threat.
Understanding communication protocol
One of the primary causes, the third-party consumable chips do not present a cyber security risk lies in their “One-way communication protocol”. In a specific printer-chip interaction:
- The printer (host) starts all communication and controls.
- The consumable chip (slave) can only respond to the requests of the printer; It cannot send data independently or execute the command independently.
This architecture ensures that a consumption chip cannot push malware, viruses or unauthorized software on the printer, making it highly impossible that these chips can be attacked as a vector.
Strong safety measures in printer chips
Printer consumable chips also include strict authentication and encryption protocols to prevent unauthorized access. It should be before a chip can work within a printer:
- Certain the printer itself using a safe, built -in algorithm.
- Encrypt all data, ensuring that there is no unauthorized amendment.
- Passing through verification by the printer, which blocks communication if the authentication fails or appears with data tampering.
These safety measures effectively eliminate the possibility of a third party chip offering malicious codes in the system.
Limited storage capacity prohibits hazards
Another reason that is unlikely to pose a threat to a cyber security, has a very limited storage capacity. Many printer-containable chips use-specific integrated circuits (ASIC)-using based desired designs, with storage as small as 8 bytes. This amount of storage is very low:
- Store or execute malware.
- Act as a functional attack vector.
- The facility of large -scale safety violations.
Even if an attacker wanted to take advantage of a printer consumable chip as a malware carrier, the hardware limits make such an attack impractical, if not impossible.
No direct network access
Perhaps the most important factor to deny cyber security concerns is that printers have no direct network access in consumable chips. The chip-to-printer interface is completely different from the printer’s internet connection, which means chip:
- Can not communicate externally.
- Network cannot act as gateways.
- Can not serve as an entry point for cyberattacks.
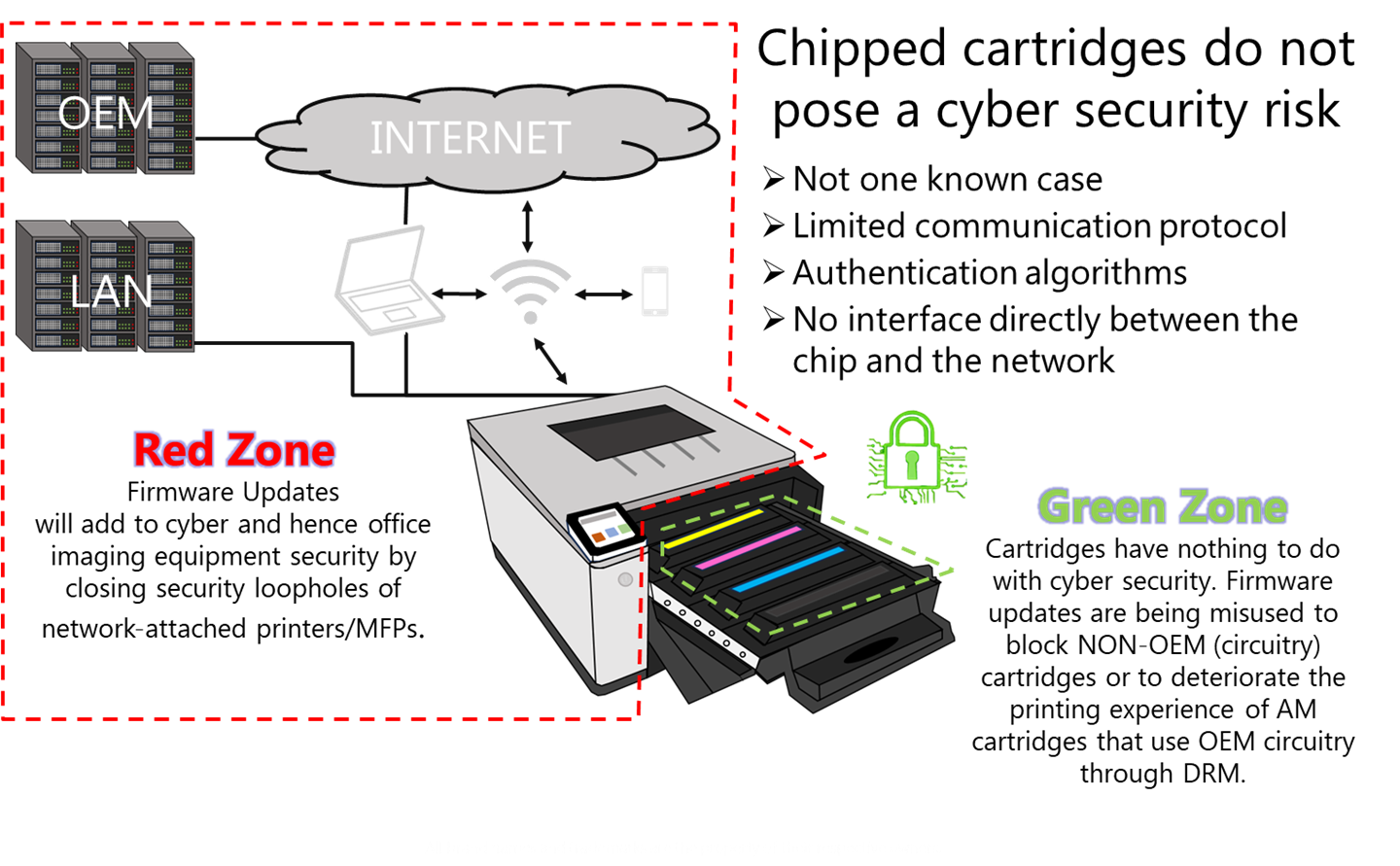
Real printer security weaknesses are found elsewhere
While cyber security risks in network devices are real, printer safety issues are more likely to be stem from weaknesses within the printer itself, not from third -party consumable chips. Many previous security violations have proved this point:
- HP Lasergate Printer Information Campaignment Vulnerance (CVE-2010-4107): A defect in the Printer Job Language (PJL) interface allowed the attackers to reach the interior file system of a printer, leaking potential data.
- HP Printer Information Campaignment Vulnerance (CVE-2023–1707): A vulnerability in HP’s Futuresmart Firmware enabled the attackers to disrupt sensitive data transmitted between HP printers and network devices.
- Eight-year-old HP Printer Demonstration (CVE-2021-39237): In 2021, researchers discovered a long-standing defects that affecting about 150 HP printer models, highlighting sensitive device data.
These cases underline the fact that the actual security risk in the printer comes from network weaknesses and firmware issues, not consumable chips.
Business purpose behind OEM security concerns
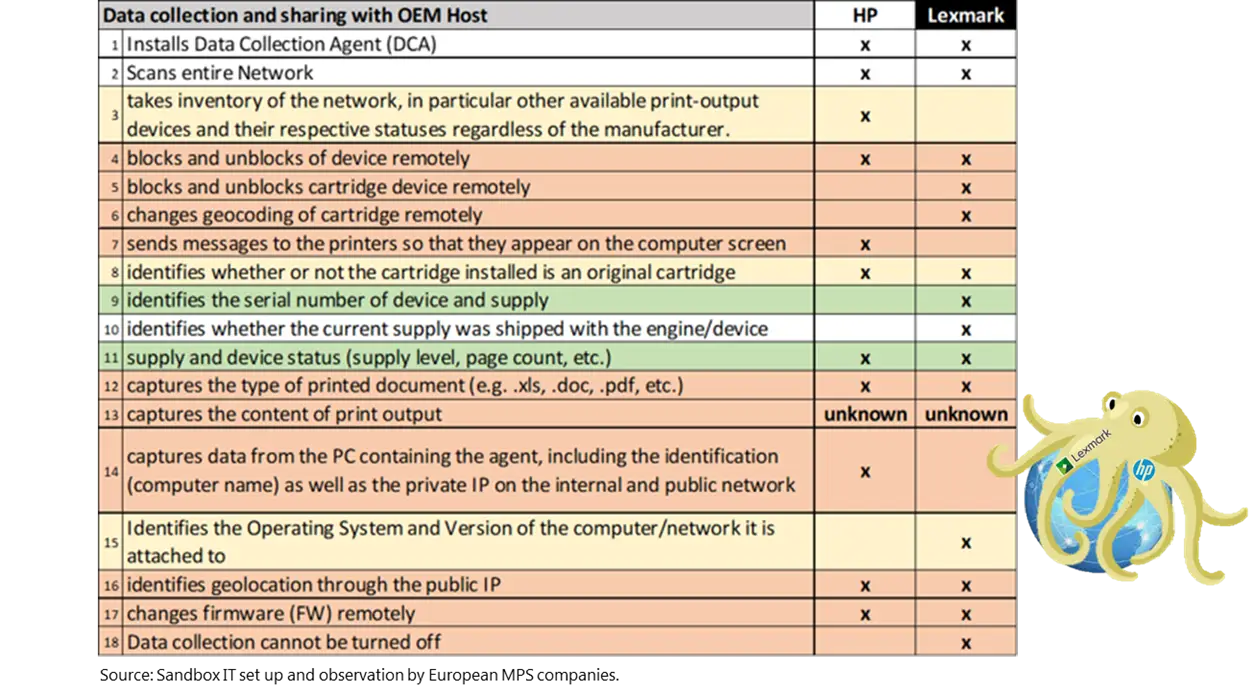
While the OEM claims that their safety concerns are about the safety of users, it is important to consider their broad business strategies. Many OEMs have integrated remote data collection in their printers, allowing them to:
- Collect user data for service adaptation.
- Monitor printing habits for market analysis.
- Control consumables through firmware updates.
These abilities increase valid concerns about privacy, competition and monopoly control rather than real cyber security hazards from third-party chips. Emphasis on perceived security risks may be more about restricting competition in consumable market rather than real user security.
In fact, third-party printers consumable chips do not take a cyber security risk. With their one-way communication, strong encryption, minimal storage and lack of network access, these chips cannot only be exploited as the entry points of malware carrier or cyber attack. True safety in printing ecosystem lies within the printer themselves in the weaknesses of the danger network, firmware defects and insufficient security protocols themselves.
While the printer security is an important issue, it is claimed that the chopped cartridge introduces cyber security risks, roughly a misleading narrative by OEM. Users and businesses should severely evaluate such claims and do not allow them to justify the competition or consumer choice.
Other stories by Volcar:
Limited life for nebilt cartridge
Myth Debanking: Why Fide Printer Cartridge is no real cyber security threat
Comment:
Please leave your comment below for the story “Myth Debanking: Why Fide Printer Cartridge is no real cyber security threat,



 Volkar o. The Cupus Dalamp has COO. He has a university degree in international management, marketing and organizational psychology from the University of Hamburg as well as a postgraduate degree in professional morality from Hegan University.
Volkar o. The Cupus Dalamp has COO. He has a university degree in international management, marketing and organizational psychology from the University of Hamburg as well as a postgraduate degree in professional morality from Hegan University.