Clickfix is a social engineering trick that hackers are more and more used to spread malware since the beginning of 2024.
This makes you stupid to run malicious commands on your computer, and the attack is now more common than ever. Hackers are getting people to install password-fetus malware, which they press a series of keyboard shortcuts, all the excuses to prove that they are not bots.
Bots are automatic computer programs that do online reiterate functions, often imitating human behavior. To prove you that they are not bots, hackers take advantage of your lack of understanding of these automated systems, so that you can inadvertently install malware.

Laptop (Kurt “Cybergui” Notson)
What you need to know
As reported CrabsnsuariThe latest clickfix campaign tricks you in installing password-chori malware under the guise of a routine “verify that you are a human” testing. Initially seen in targeted attacks, it has now gone into the mainstream, affecting industries such as hospitality and healthcare.
The scam begins when you visit a hack or malicious website and see a fake captcha-style prompt. Clicking on the “I am not a robot” button triggers a set of instructions, which asks you to press the specific keyboard shortcut. First, you are asked to press Windows + R, which opens the Windows run dialogue. You are then instructed to suppress Ctrl + V, which paste a malicious script copied from the virtual clipboard of the website. If you press the enter, a script is executed that downloads and drives malware.
What is Artificial Intelligence (AI)?
Cyber criminal phishing emails and malicious websites are used to spread clickfix. The hospitality industry has been heavily targeted, with the attackers with implementing booking.com and sending fake emails referring to guest reviews or promotions. By clicking on the link in these emails you include a clickfix mesh. Healthcare workers are also targeted, embedded in the physical therapy site hep2go used widely with malicious codes.
Once the clickfix is on your PC, it installs a variety of malware, including password steeler such as Xworm, Lumma Stealer and Danabot, which removes your login credentials and financial information. Some versions provide remote access trozons such as Venomrat and Esinkrat, giving the attackers complete control over your system. Other people deploy netsupport rat, a remote access tool that is usually misused for cyber espionage.
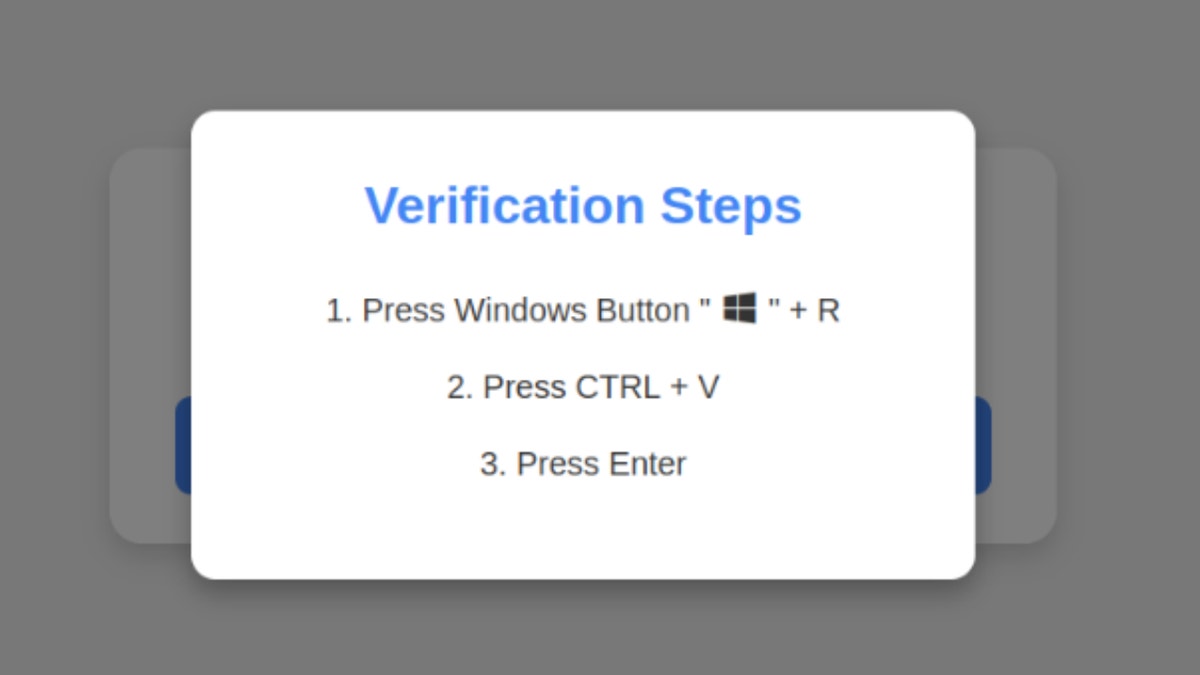
Performing this series of keypresses inspires Windows to download password-fetus malware. (Krebsnsurity)
Hidden cost of free apps: your personal information
Previous clickfix attacks
Security researchers believe that the Clickfix has been targeting people since March 2024. I reported back to malware in June 2024 Fake Google Chrome, Word and ONEDRIVE Arrived as presented To trick users in downloading harmful codes. Like the current expedition, the attackers inspired the victims to click on a button, which mimicked a powerrashel “fix” on the clipboard, then paste and run it to the run dialogue or powerrashel prompt.
By November 2024, attacker Extended its goals from GoogleThe scam started with an email in which the Links of the Google Meat Session, often disguised to appear as it was from the organization’s organization. This link leads to an invitation for a meeting, webinar or online cooperation. Clicking on the link was directed to the victim on a fake Google Meat page, showing a warning claim that there was a problem with his PC, such as problems with his microphone, camera or headset.
The attack was also seen in fake chrome error pages and Facebook login signals, further spread malware to various platforms and increased its reach.
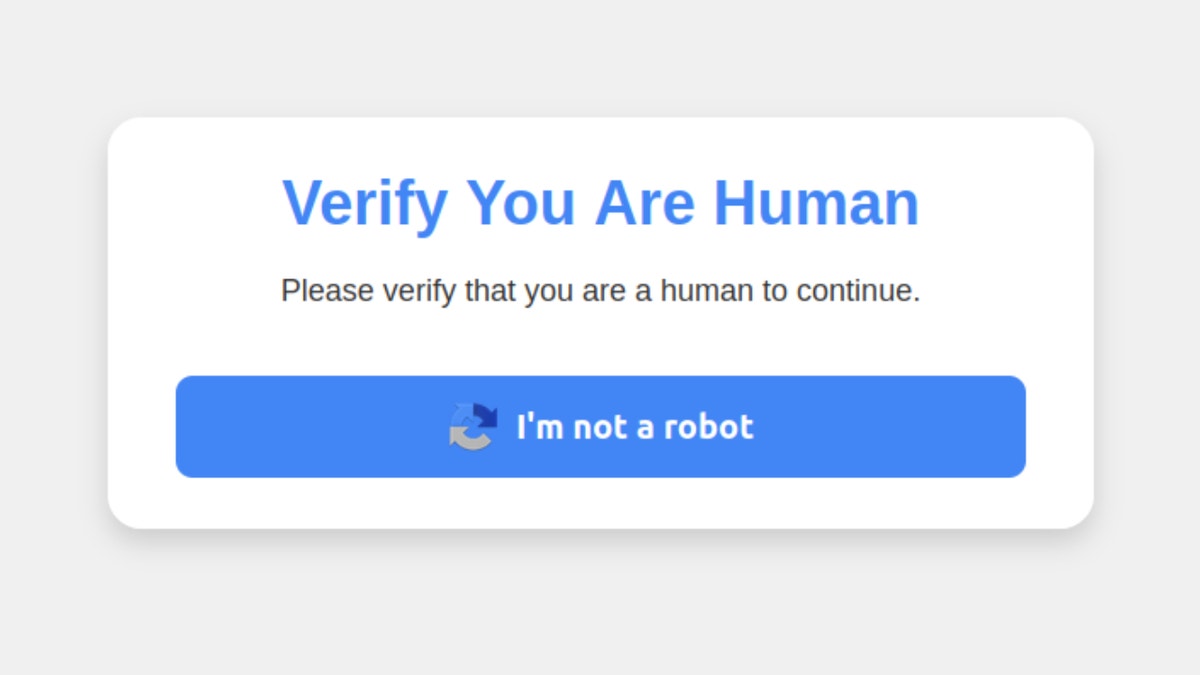
This malware attack pretends to be a captcha that aims to separate humans from the bot. (Krebsnsurity)
External hackers who are out to steal your identity
6 ways you can be safe from clickfix malware
Clickfix to protect themselves from the developed danger of malware, which continues to target users through sophisticated social engineering strategy, consider implementing these six essential security measures.
1. Captcha signs doubt: Valid captcha tests never require you to press Windows + R, copy the command or do anything. If a website instructs you to do so, it is a scam. Close the page immediately and avoid interacting with it.
2. Do not click on the link from rejected email and use strong antivirus software: Many clickfix attacks begin with fishing emails that apply reliable services such as Booking.com or Google Meat. Always verify the sender before clicking on the link. If an email seems necessary or unexpected, go directly to the company’s official website instead of clicking on any link inside the email.
Get Fox Business when you click here
The best way to protect yourself from malicious links that installs malware, potentially reaches your personal information, is a strong antivirus software installed on all your devices. This security can also make you alert for email and ransomware scams, keeping your personal information and digital assets safe. Get my pics for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices,
3. Enable two-factor authentication: Able Two-factor authentication whenever possible. It adds an additional layer of safety by the need for a second form of verification, such as codes sent to your phone, in addition to your password.
4. Keep the equipment updated: regularly Update your operating system, browser and security software Ensures that you have the latest patches against the known weaknesses. Cyber criminals exploit chronic systems, so it is a simple but effective way to enable automatic updates.
5. Monitor your accounts for suspicious activity and change your password: If you have interacted with a suspected website, fishing email or fake login page, check your online accounts for any unusual activity. Look for unexpected login efforts, unauthorized password reset or financial transactions that you do not recognize. If anything closes, change your password immediately and report the activity to the respective service provider. In addition, consider using a password manager to generate and store complex passwords. Find out more about me 2025 Best Expert-Recipe Password Managers,
6. Invest in personal data removal service: Consider using a service that monitors your personal information and alerts you for potential violations or unauthorized use of your data. These services may provide an initial warning indication of identity theft or other malicious activities as a result of clickfix or similar attacks. While no service promises to remove all your data from the Internet, if you want to continuously monitor and automate the process of removing your information from hundreds of sites continuously over a long period, a removal service is very good. See my top pics for data removal services here,
Large -scale safety defects put the most popular browser at risk on Mac
Kurt’s key to Techway
Clickfix is a reminder that malware does not always rely on complex exploits. This often requires you to follow the wrong instructions. The attackers are refining their ways, fake captcha, fishing email and misleading pop-up scams are more assured than ever. The best way to stay ahead is anything that seems a bit away. If a website asks you to run the command or paste something in the powerrashel, it is a red flag. If an email pressures you to click on the link, verify it first.
Click here to get Fox News app
Do you think tech companies are doing enough to stop malware like clicks? Write us and tell us Cyberguy.com/Contact.
For my tech tips and security alert, subscribe to my free cybergui report newsletter Cyberguy.com/newsletter.
Ask Kurt a question or tell us which stories you want to cover us.
Follow Kurt on your social channels:
Answers to the most asked cyber questions:
New from Kurt:
Copyright 2025 cyberguy.com. All rights reserved.


