Cyber criminals are constantly looking for new ways to take advantage of reliable apps and browser extensions.
Since people rely on devices that seem valid, the attackers use them to spread malware or steal sensitive data. A new report suggests that more than 3.2 million users have been affected by a safety violation that includes malicious browser extensions.
These extensions, which appeared real, were secretly embedding harmful scripts, stealing data and manipulating the search results.
Be preserved and notify! Get safety alerts and expert take tips – Now sign up for Kurt’s Cybergui report
A man using a chrome browser. (Kurt “Cybergui” Notson)
How was the extension compromised?
Gitlab security A network of compromised browser extensions has exposed a major security violations affecting more than 3.2 million users, including some associated with Gitlab. The attack stems from a supply chain violation, where danger actors infiltrated valid extensions and pushed malicious updates. These updates embedded hidden scripts who allowed unauthorized data collection, replaced HTTP requests and injecting advertisements in web pages, without notice to all users.
Originally designed for tasks such as AD blocking, emoji input and screen recording, these extensions were re -presented through secret updates, exploiting comprehensive permissions given by users, enabling the real -time manipulation of web activity.
Typically, malicious extensions or apps are made only to steal data, a way of being listed in an official store after their advertised functionality. This was not the case here. These were valid extensions that became harmful only after the attackers injected malicious updates.

Depiction of a hacker at work (Kurt “Cybergui” Notson)
Hidden cost of free apps: your personal information
Which extensions are affected?
Many of the compromised extensions are usually used and may be present in your browser. For example, ad blockers such as Adblock are considered valuable to eliminate disruptive advertisements and increase browsing privacy. However, in this violation, these devices were manipulated to give malicious payloads. The following extensions have been identified as affected:
- Blipshot: Takes full-page screenshots with one click
- Emojis – Emoji Keyboard: Provides an emoji keyboard for easy access
- Watoolkit: A toolkit for WhatsApp web
- Color Changer for YouTube: Allows optimization of YouTube’s color scheme
- Video effects to increase youtube and audio: Adds effects and increases audio for youtube videos
- Theme for Chrome and YouTube ™ picture in the picture: Theme and picture-in-picture provides functionality
- Mike adblock fur chrome: A German advertising inhibitor for chrome
- Page refresh: Automatically refreshes web pages
- Vistia video downloader: Vistia enables video download
- Super dark mode: Provides a dark theme for websites
- Emoji Keyboard Emojis for Chrome: Another emoji keyboard for chrome
- ADWOC for Chrome – Noads: Blocks advertisements while browsing
- Adblock for you: Another advertising-blocking extension
- Adblock for Chrome: Still another advertising blocker for chrome
- Quick capture: A tool for capturing web materials
- Kproxy: A proxy service for anonymous browsing
If any of these extensions are installed on your browser, it is recommended that you assess their permissions and consider their removal until the official security update is verified.
The malicious extensions ignored the material safety policy safety, designed to prevent cross-site scripting attacks, allowing the attackers to modify the web content without detecting. He also interacted with the command-end-control server to get further instructions, showing the high level of coordination. The attackers exploited the location of trust users in the Chrome web store and its automatic update systems. The investigation shows that this activity has been going on at least from July 2024.
Clarification on affected extension
Some compromised extensions listed above have common names that may be similar to the famous and legitimate devices, but they are not the same. For example, in our list, “Password Manager” refers to malicious extensions identified in violations, not the prestigious password manager services We mention hereSimilarly, in this context, an extension called “Edblock Plus” or “VPN Extension” is not necessarily widely reliable versions, but rather copy or malicious variants.
Follow these steps to ensure that you are using a valid expansion.
- Verify the developer -Always check for the publisher of the extension in the Chrome web store or firefox add-on. Official brands like Norton, Google or Microsoft will be clearly listed.
- Check reviews and download – In malicious extensions, there are often low ratings, generic reviews or less number of downloads than their legitimate counterparts.
- Avoid third-party sites -Install a browser extension directly from trusted sources such as Kaval Chrome Web Store, Mozilla Add-on or Developer’s official website.
- Monitor for unusual behavior – If an extension starts requesting excessive permissions or begins to behave separately (eg, injecting advertisements, slowing down browsing), then this compromise can be made.

Google Chrome on a smartphone (Kurt “Cybergui” Notson)
From tickets to trouble: how your online data can be made weapons against you
How to extract extension from Google Chrome
If you have installed one of the above extensions on your browser, remove it as soon as possible. To remove an extension from Google Chrome, follow these steps.
- Open chrome And click IconYou will find it in the top-right corner of the browser.
- Now you can see all active extensions. Click Three dots icons Next to the extension you want to remove and choose Remove from chrome,
- Click Removal To confirm.
What is Artificial Intelligence (AI)?
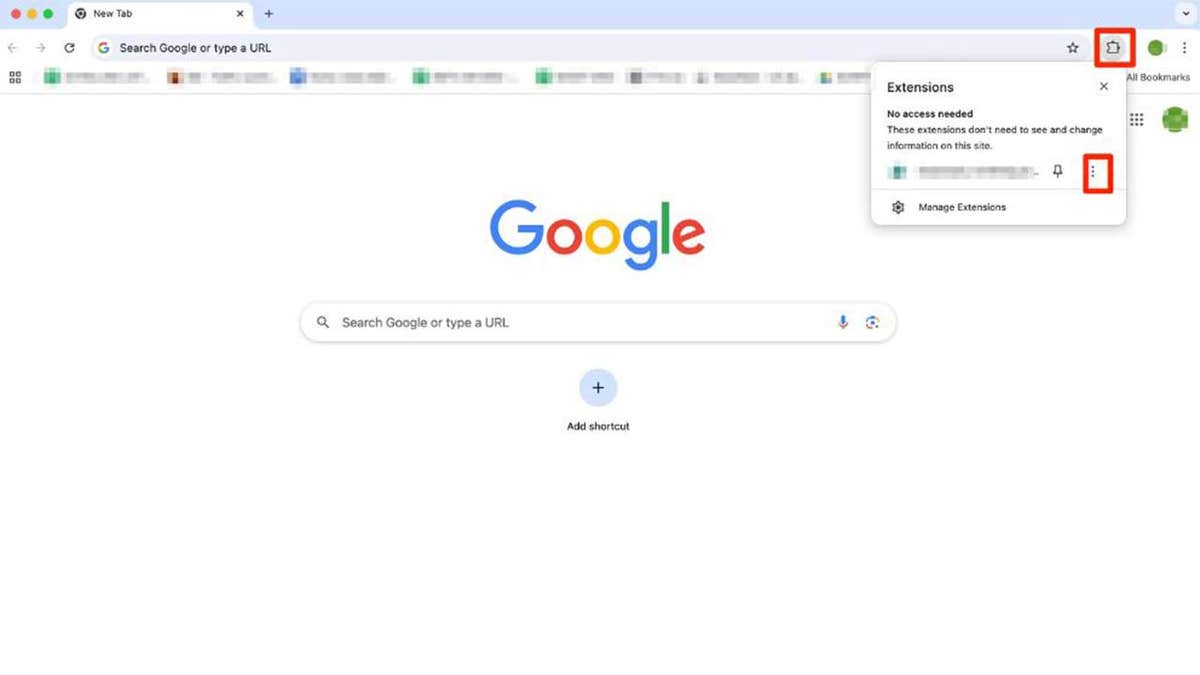
Steps to remove an extension from Google Chrome (Kurt “Cybergui” Notson)
6 ways you can protect your personal data
Here are 6 ways to protect your sensitive information and maintain your online privacy:
1. Keep your browser and extension up -to -date: The old software is a goldmine for cyber criminal. In older versions of your browser or extension, bugs or safety intervals can be exploited to inject malicious code, steal data or take control of your system. Updates patch these weaknesses, making them an important line of defense. Turn on automatic updates for your browser (eg, chrome, firefox, edge) so that you are always running the latest version without thinking about it. See my guide Update your equipment and app For more information.
2. Establish extensions from only reliable sources: Official browser stores such as the Chrome web store or Firefox Ad-on have rules and scans to catch bad actors, but they are not correct. Extension from random websites or third-party downloads is more likely to hide the extension malware or spyware. Stick to the official store for your browser. Do not download the extension from the sketch link.
3. Strong antivirus software is: The best way to protect yourself from malicious links that establishes malware, potentially reaches your personal information, is to install antivirus software on all your devices. This security can also make you alert for email and ransomware scams, keeping your personal information and digital assets safe. Get my pics for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
Get Fox Business when you click here
4. Doubt the extension requesting unnecessary access: Some extensions overch over the purpose. A calculator tool is asking for your browsing history or a Weather app that your login data is a huge red flag.
Before installing, ask, “Does this permission matches the job of extension?” If there is no answer, do not install it. As long as it is clearly not appropriate (eg, a password manager). If an update suddenly adds new permission requests, then why dig. This may mean that the extension has been sold or hacked.
5. Update your password: Change the password for any account that can be affected by the event, and use unique, strong passwords for each account. Consider using a password manager. This can help you generate and store strong, unique passwords for all your accounts. Find out more about me 2025 Best Expert-Recipe Password Managers,
6. Remove your personal data from the public database: If your personal data was exposed in this security incident, it is important to work quickly to reduce your risk of identity and reduce your risk of scams. While no service can guarantee the removal of your data from the Internet completely, a data removal service is actually a smart option. They are not cheap nor your privacy. These services do all the work for you by actively monitoring and systematically monitoring your personal information from hundreds of websites. This is what gives me peace of mind and has proved to be the most effective way to eradicate your personal data from the Internet. By limiting the available information, you reduce the risk of cross-referring data from breech to scams cross-referenceing data, which they can find on the dark web, making it difficult for them to target them. See my top pics for data removal services here,
Large -scale safety defects put the most popular browser at risk on Mac
Kurt’s major takeaways
Browser extensions can improve functionality, but can also cause significant safety risks if not carefully managed. If you have any of the above extensions installed in Chrome, you should remove them immediately. Consider your browser to be an important part of your digital security. Check your extension regularly, remove unnecessary permissions and be cautious about automatic updates from reliable sources.
Should browsers implement strict restrictions as to what to extension by default? Write us and tell us Cyberguy.com/Contact.
Click here to get Fox News app
For my tech tips and security alert, subscribe to my free cybergui report newsletter Cyberguy.com/newsletter.
Ask Kurt a question or tell us which stories you want to cover us.
Follow Kurt on your social channels:
Answers to the most asked cyber questions:
New from Kurt:
Copyright 2025 cyberguy.com. All rights reserved.


